Deliverability
Gmail Promotions tab: A guide to optimize email delivery
Many marketers hate Gmail’s Promotions tab. But its unique features might be a secret asset for email senders. We’ll tell you how it works and how to make the most of it.
PUBLISHED ON
The Gmail Promotions tab’s hot debut in 2013 caused mixed reactions. Some marketing pundits predicted that it marked the end of email marketing as we know it. Others were less dramatic and just stated that it would have a negative impact on the opens and clicks of bad marketing campaigns.
A lot has happened since. Nowadays, email campaigns need to be more inventive than ever in order to stand out, and many marketers have started to find value in Google’s Promotions tab features, as a way to incorporate more visual elements right in the inbox.
So, in this article, we’ll explain what the Gmail Promotions tab is, why it’s useful for marketers, and how to make the most of its features.
Table of contents
Image Preview
Deal Annotation
Product Carousel
Expiration date
Logo URL
Directly edit Google’s script
Use an Annotations markup helper
What is the Gmail Promotions tab?
Personal inboxes are often crazy and chaotic. As marketers and users, this is something we know well – and so does Gmail.
That’s why, over a decade ago, Gmail set out to change the inbox experience forever by rolling out tabs to organize emails based on their content and sender address. Gmail accounts that have tabs enabled – around half of Gmail users based on our 2021 Email Engagement report – have their emails sorted into these tabs for better inbox organization.
Gmail’s Promotion’s tab was one of the first tabs launched in 2013. This tab acts like a folder within the Gmail inbox that segments and classifies marketing and commercial emails.
Gmail’s algorithm uses the content of the email and the sender address to sort out incoming emails into tabs. That’s how marketing campaigns and other bulk emails are identified and placed in the Promotions tab.
Aside from the Promotions tab, Gmail also incorporated other inbox tabs to categorize email content:
Primary tab: Includes the most important emails and urgent notifications. The Primary tab is meant for personal emails and any other messages that don’t fall into any of the other tabs.
Social tab: For messages and email notifications from social media apps like Facebook, Twitter, or Instagram.
Updates tab: For transactional email messages such as shipping notifications and purchase confirmations, as well as email updates on changes to shared Google documents.
Forums tab: Includes messages and updates from discussion forums, groups, and other mailing list notifications.
Gmail tabs offer a more organized inbox experience for users. And while many senders see tab placement as an email marketing challenge, the truth is these folders offer opportunities for marketers beyond what many unclassified inboxes can deliver.

Promotion annotations on mobile
Using Email Schema Markup, senders can add code snippets to their email campaigns to allow Gmail to better identify different elements within the content and take advantage of some of these advanced features.
Thanks to this schema and its machine learning algorithms, Gmail identifies messages that could interest subscribers based on their filters, classifies them by topic or theme, and identifies the elements to display.
Unfortunately, there’s no way to know how to get to the top of the Promotions tab and the system for getting Annotations, even with the right script implementation. We’re sure that, over time, these tricks will be uncovered – so be sure to stay on top of these opportunities.
What elements can be displayed in the Gmail Promotions tab?
The Gmail Promotions tab offers a much more visual interface to bring your emails to life with images, deals, expiration dates, and more. Using the Schema Markup, senders can add badges, carousels, and image previews to highlight the key elements in their campaign.

A view of an email preview in the Promotional tab
Here is a list of elements that you can include in your emails:
Image Preview
Yes, email previews in the inbox can now include images. The images could be a product preview or something that really encapsulates what your newsletter is all about. GIFs are not supported, though, and neither is a text only image. Google specifies that this is a purely visual space.
Deal Annotation
Deal Annotation is a nifty feature that lets you use color and text to draw attention to your deals.
It includes two popular badges to draw attention to your offers:
Green Badge: Green is the color of money, and this badge is used to clearly display your offer. Avoid writing long sentences that will be cut off – opt for messages such as “Free Delivery”, “20% discount”, or “Deals” instead.
Grey Badge: The grey badge shows a promotional code that the user can use to access their discount. If there is no code, including it is not just unnecessary, but not recommended as the word ‘CODE’ will always preface any added text.
Product Carousel
Product carousels can have up to 10 image previews, but you can’t have duplicate images. Each unique photo acts as a linked product card, able to direct traffic to a unique URL. You also have space to add a short description and pricing details in your chosen currency.

You can create your product carousel with the script provided here.
Expiration date
The Expiration date feature is very interesting for marketers, as it allows them to create a sense of urgency by adding an expiration date to a deal.
This feature lets an email be visualized on top of a group twice: Once when it gets sent the first time, and another in the final three days before expiration.
Logo URL
Brands can finally show their logos so that users will immediately be able to identify their email campaigns – even though it’s only in the email preview. Use a HTTPS URL and not a HTTP to avoid errors.
If the user clicks on any of these Annotations, this will open the email.
Gmail will also show a preview of the Promotional tab in the Primary inbox. This is another great reason to enable Annotations in your email campaigns.

Teasers with logos are added to the Primary tab to highlight top emails in the Promotions tab.
How to use the Gmail Promotional tab to your advantage
After validating the sender domain with Google, there are two ways to appear at top of the Promotions tab.
Directly edit Google’s script
Email developers simply need to modify the code given by Google and generate a preview using the code provided on this page. Once changed, you can include the email code in your campaigns.
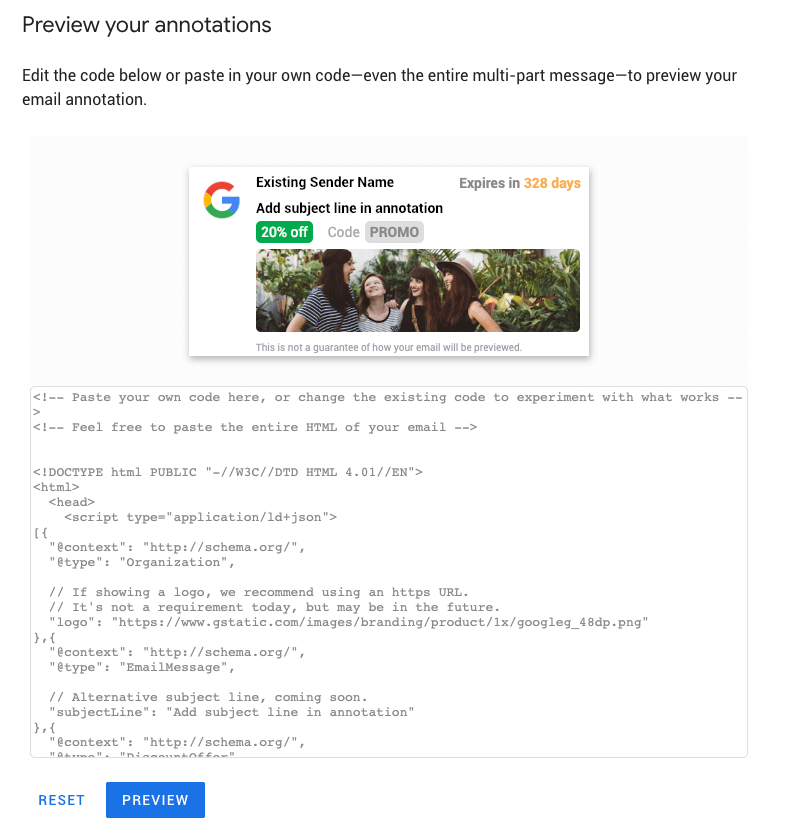
Preview your Annotations with this Google tool.
Use an Annotations markup helper
Non-technical email marketers can use Google’s Structured Data Markup Helper or other Annotations editors to create the code. These editors make it easier for senders to add, identify, and tag relevant details (logo, image, subject, offer, etc.) in the required field to personalize the Annotation.
Once created, the code can be downloaded in Microdata and insert it in the body tag of their email campaigns, or in JSON in the body or head tags.

Google’s Structured Data Markup Helper can help create Annotations HTML code for email.
Still want to avoid the Gmail Promotions tab and get emails into the Primary inbox?
Even if it is impossible to know exactly how Gmail’s algorithm works, there are some best practices to maximize your chances of landing into the Primary tab.
But, before doing anything else, think about your brand mission and objectives first and foremost and consider if these campaigns really deserve to be in the Primary inbox. After all, the Promotions tab may not be a bad thing for your subscribers, who expect to see marketing emails in that tab.
Think of the Primary tab as the figurative home of the user, where they meet family and friends. Imagine how creepy it would be for a marketer to just barge into their home with a cool discount. Trying to place promotional emails in the Primary tab could easily lead to unsubscribes and spam complaints that could severely hurt your email reputation and deliverability.
If you are sending marketing emails, we highly recommend you do not try to cheat Gmail’s filtering algorithms, or risk getting your future campaigns in the spam folder.
That said, some transactional emails that contain password resets, order confirmations, and other important notifications perhaps belong in the personal feed.
If you are looking to send to the Primary tab, here are some tips on how to avoid the Promotions tab:
Don’t use commercial or marketing phrases: Forget CTAs like "Buy Now” and other words like discount, promotion, or offer. These will activate the filters.
Keep images to a minimum: Email marketing campaigns tend to have more images than personal ones, so it’s an easy flag.
Use text-based email campaigns: Most marketing emails are HTML-based, so try to opt for plain text emails.
Keep the links to a minimum: It doesn’t seem personal to have too many links.
Personalize your email: Referring to the subscriber by their first name would be a way to show Gmail that you know them personally.
Send short emails, hopefully resembling the ones you send to your colleagues.
Don’t use a generic reply-to addresses such as contact@ or support@ and
Configure your SPF and DKIM authentication records to avoid getting seen as a spammer: to learn more, here is our guide on authenticating domains with SPF & DKIM.
These are just general tips to help you avoid the Promotions tab, but there’s no guarantee that your campaigns would be classified as Primary. So, we recommend you don’t fight it – just embrace the benefits of the Promotions tab!
Embrace Gmail’s Promotions tab as marketing opportunity
The Promotions Tab has exceeded the expectations of skeptics and email marketers everywhere by being more optimized for marketing emails and therefore conversions. After all, Gmail doesn’t want email marketing to die, they want it to thrive for both the user and brands.
If email marketers know how to take advantage of this Promotions Tab, then they can really do some new and innovative things to attract and retain customers.
If you want to know the latest updates on this, don’t hesitate to subscribe to our newsletters, we’ll have more updates down the line!